
In December of 2020, the US government and numerous private organizations discovered that they were the targets of a cyberattack. The consequences of that attack, known as “Solar Winds,” will take many years to understand and learn to protect against. This is a massive problem for two major reasons: the hackers, who were believed to be affiliated with Russian Intelligence, were able to gain access for a long period of time without being detected, and it will also take a long time for security experts to determine the extent of what has been compromised.
To try and comprehend the ramifications of this, please engage in the following thought exercise with me. Imagine that your work and personal computers had been compromised. If this were true, stop and think of all of the things you would need to do to protect yourself, and how it would require you to change how you operate moving forward?
Many people today have had brushes with identity theft which is a horrific experience. A cybersecurity breach of this nature magnifies that tragedy even further because not only is your identity and financial security compromised, but so is all your proprietary information, and that of your employer and corresponding contacts’ communications.
Fragments of these cybersecurity attacks can sit dormant for months, and years, and only revive when the author wants them to begin their exploit. This type of stealth hack is the most worrisome aspect of these attacks and is forcing security administrators to re-evaluate everything about how they go about securing their protocols, information, data, and networking.
Because of these recognized vulnerabilities in security infrastructure, analysts foresee a seismic increase in spending which will be earmarked specifically to patch cybersecurity threats. Due to the pandemic and economic lockdown many workforces are still operating remotely and will continue to do so well into the future. It is critical to ensure that employees working remotely do not create vulnerabilities to their employers networking protocols. Any such event can create potentially catastrophic consequences to the integrity and security of a network.
Analysts are still determining the scope of the “Solar Winds” attack, but it promises to be much larger than originally expected. The source of the attack is believed to be a widely popular piece of server software called SolarWinds. This software is used by 300,000 customers around the world, including all five branches of the U.S. military, the Pentagon, the State Department, NASA, and National Security Agency, the Department of Justice, and the White House.
The long and short of these data breaches is – it is going to change how commerce is conducted and what authentication methods will be used to prevent horrible things from happening to data.
Recently, four exploits were found in Microsoft’s Exchange Server software that have reportedly led to over 30,000 US governmental and commercial organizations having their emails hacked These exploits have been patched by Microsoft, but security experts say that the detection and cleanup process will be a massive effort for the thousands of state and city governments, fire and police departments, school districts, financial institutions, and other organizations that were compromised.
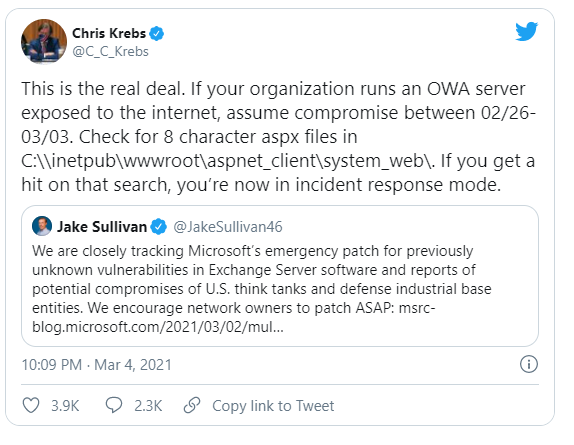
I created a Google alert on basic Cybersecurity terms. The results I received were downright horrifying and highlights how broad and sweeping in scope these data breaches have become. Cybersecurity affects all companies, large and small, that engage in commerce.
Judge for yourself:





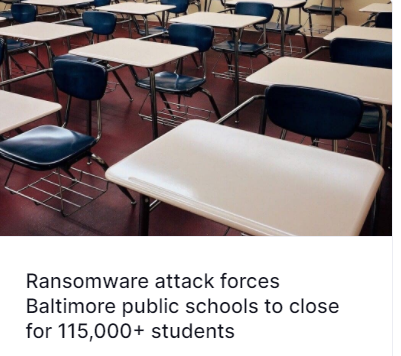

The battle lines are clearly drawn, and the time has come for the white hats to create technology and protocols that put the black hats on defensive. That, in essence, is the opportunity that Cybersecurity presents in present time.
One ETF which provides a barometer of this sectors potential is:
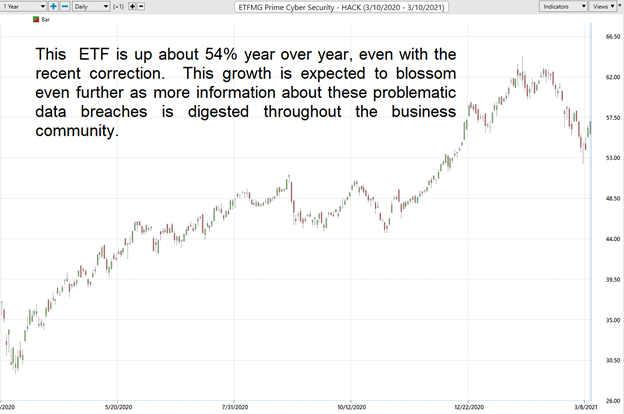
ETFMG PRIME CYBERSECURITY ETF HACK
This ETF is up about 54% year over year, even with the recent correction. This growth is expected to blossom even further as more information about these problematic data breaches is digested throughout the business community.
It might help to put Cybersecurity stocks on your radar. As I write this, some Cybersecurity stocks are in downtrends. However, monitor the artificial intelligence forecasts for updates for when they recover, they will be a major force to contend with and will most likely prove to be the strongest sector in the market, as all businesses scurry to secure their data.
Horrible as they are, these attacks serve as a huge tailwind for the growth of the Cybersecurity industry.
If you are searching for a silver-lining in all this, I would point toward the inevitable growth of the Cybersecurity investment sector. The 1-click way to get investment exposure to this inevitable trend is through the ETF, HACK.
But as traders we would urge you to pay attention to the A.I. forecasts as this sector’s volatility is fast and furious.
Remember that A.I. is so powerful because it learns what doesn’t work, remembers it, and then focuses on other paths to find a solution. This is the Feedback Loop that is responsible for building the fortunes of every successful trader.
Artificial Intelligence applies mistake prevention as a continual process 24 hours a day, 365 days a year towards whatever problem it is looking to solve. A.I. is particularly powerful at forecasting changes in volatility as well.
It’s a game-changer and a winning combination.
Find the trend in volatility.
Scrutinize the 1–3-day forecast.
Enter a risk managed position with very limited risk…
Be beautifully positioned before the herd even knows what happened.
Lather. Rinse. Repeat.
The Answer A.I. offers may surprise you.
This is how small traders grow their accounts by finding small exploitable niches where they have a unique, distinct advantage. VantagePoint now forecasts for stocks in our new Cybersecurity Stock Sector. I recommend you come check them out.
Today Artificial Intelligence, Machine Learning and Neural Networks are an absolute necessity in protecting your portfolio.
While reporters, talking heads, and analysts want to discuss esoteric economic ideas, our loyalty as traders is to the trend! This is how VantagePoint’s artificial intelligence empowers traders daily!
Intrigued? Visit with us and check out the A.I. at our Next Live Training.
Discover why artificial intelligence is the solution professional traders go-to for less risk, more rewards, and guaranteed peace of mind.
It’s not magic. It’s machine learning.
Make it count.
IMPORTANT NOTICE!
THERE IS SUBSTANTIAL RISK OF LOSS ASSOCIATED WITH TRADING. ONLY RISK CAPITAL SHOULD BE USED TO TRADE. TRADING STOCKS, FUTURES, OPTIONS, FOREX, AND ETFs IS NOT SUITABLE FOR EVERYONE.
DISCLAIMER: STOCKS, FUTURES, OPTIONS, ETFs AND CURRENCY TRADING ALL HAVE LARGE POTENTIAL REWARDS, BUT THEY ALSO HAVE LARGE POTENTIAL RISK. YOU MUST BE AWARE OF THE RISKS AND BE WILLING TO ACCEPT THEM IN ORDER TO INVEST IN THESE MARKETS. DON’T TRADE WITH MONEY YOU CAN’T AFFORD TO LOSE. THIS ARTICLE AND WEBSITE IS NEITHER A SOLICITATION NOR AN OFFER TO BUY/SELL FUTURES, OPTIONS, STOCKS, OR CURRENCIES. NO REPRESENTATION IS BEING MADE THAT ANY ACCOUNT WILL OR IS LIKELY TO ACHIEVE PROFITS OR LOSSES SIMILAR TO THOSE DISCUSSED ON THIS ARTICLE OR WEBSITE. THE PAST PERFORMANCE OF ANY TRADING SYSTEM OR METHODOLOGY IS NOT NECESSARILY INDICATIVE OF FUTURE RESULTS. CFTC RULE 4.41 – HYPOTHETICAL OR SIMULATED PERFORMANCE RESULTS HAVE CERTAIN LIMITATIONS. UNLIKE AN ACTUAL PERFORMANCE RECORD, SIMULATED RESULTS DO NOT REPRESENT ACTUAL TRADING. ALSO, SINCE THE TRADES HAVE NOT BEEN EXECUTED, THE RESULTS MAY HAVE UNDER-OR-OVER COMPENSATED FOR THE IMPACT, IF ANY, OF CERTAIN MARKET FACTORS, SUCH AS LACK OF LIQUIDITY. SIMULATED TRADING PROGRAMS IN GENERAL ARE ALSO SUBJECT TO THE FACT THAT THEY ARE DESIGNED WITH THE BENEFIT OF HINDSIGHT. NO REPRESENTATION IS BEING MADE THAT ANY ACCOUNT WILL OR IS LIKELY TO ACHIEVE PROFIT OR LOSSES SIMILAR TO THOSE SHOWN.




